A regulator, partner, or board member asks a simple question:
“How confident are we that our digital systems are secure today?”
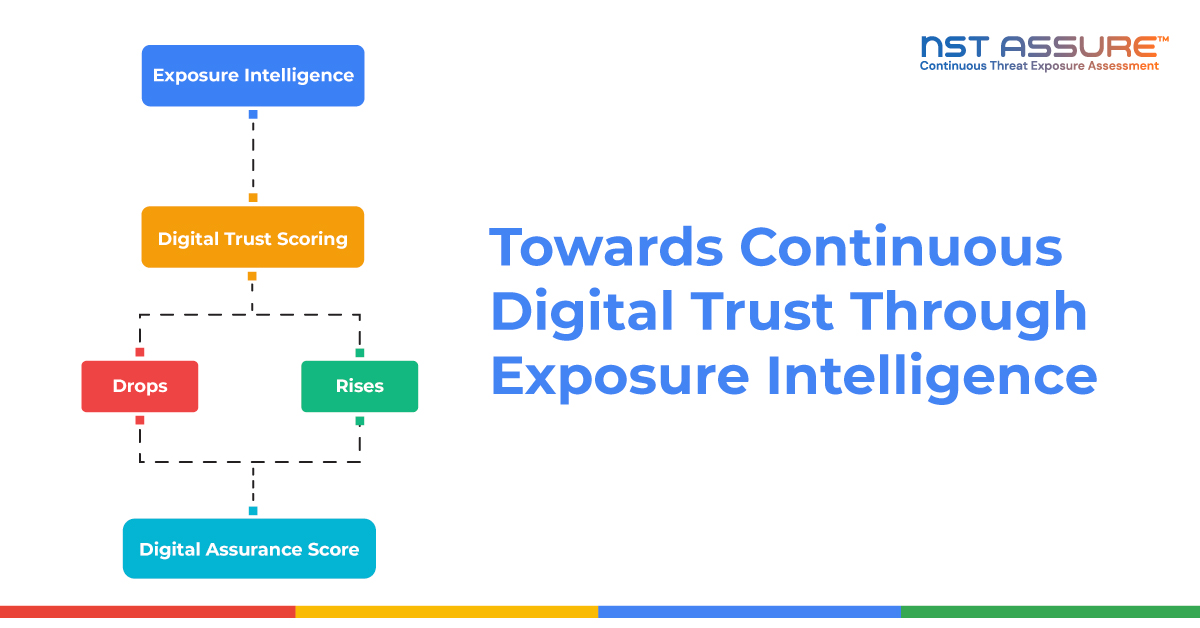
Instead of answering with the last audit report or a long list of vulnerabilities, you show a live digital trust score. That score is based on current exposure, control effectiveness, and real-world validation—not assumptions.
If exposures increase or controls weaken, the score drops. If risks are fixed and controls are proven effective, the score improves. At any point in time, the score reflects how trustworthy your digital environment actually is right now.
That is digital trust scoring.
Imagine this: your organization’s security doesn’t just react to threats. It anticipates them, fixes issues automatically, and continuously proves—to boards, regulators, and customers—that your organization is trustworthy right now.
That is the future of Exposure Intelligence evolving into Digital Trust Validation, powered by AI. What begins today as real-time aggregation of data from attack surfaces, vulnerabilities, controls, and threat signals will evolve significantly between 2027 and 2030.
With AI-accelerated cyber threats, continuous digital trust is becoming the new gold standard. The days of annual audits or static “secure” certifications are over.
Continuous digital trust means real-time, verifiable proof that your organization, systems, data, and interactions remain trustworthy—every moment, every day—through ongoing validation of controls, exposures, and resilience.
This shift builds directly on Exposure Intelligence: aggregating live data from attack surfaces, vulnerabilities, controls, and threat signals to produce contextual, actionable risk insight. As threats evolve faster than humans can respond, AI transforms this intelligence into predictive, autonomous assurance.
1. Predictive and Proactive – AI Sees Risk Before It Materializes
Today’s tools show where exposures exist today. Tomorrow’s AI predicts where exposure is likely to emerge next. By combining environment simulations, global threat intelligence, attacker behavior, and real-world exploit trends, AI forecasts risks—such as new exploit paths or weakening controls—before they are actively abused.
As confidence increases, low-risk actions can be handled automatically: isolating exposed assets, adjusting policies, or applying fixes—without waiting for human intervention.
2. Autonomous AI Agents Drive Continuous Validation
Security increasingly operates through coordinated AI agents:
- →One agent continuously discovers assets and exposure changes
- →Another models attack paths in real time
- →A third validates whether controls actually prevent exploitation
- →A fourth translates exposure into business impact and risk
These agents learn from every cycle and continuously refine decisions. This is the evolution of Continuous Threat Exposure Management (CTEM) toward self-healing security. Digital trust becomes evidence-based and measurable, not assumed.
3. Digital Trust as a Measurable Business Signal
AI shifts security from technical metrics to a business-relevant trust signal. Instead of asking “How many vulnerabilities do we have?”, leaders can see:
- →A live trust score based on current exposure and control effectiveness
- →The impact of fixing or ignoring specific risks
- →How trust changes over time as conditions evolve
Boards begin to treat digital trust as a KPI—just like financial or operational health. Higher trust supports faster decisions, stronger partnerships, and continuous regulatory confidence.
4. From Validation to Continuous Proof
Between 2026 and 2028, the gap between knowing your exposure and proving trust continues to narrow. Organizations using AI-driven CTEM can expect:
- →Fewer material security incidents
- →Reduced operational disruption
- →Explainable, governed AI decisions that regulators and leaders can trust
Security moves from periodic validation to continuous, defensible proof of resilience, transforming it from a cost center into a strategic advantage.
Foundational Capabilities Enabling This Transformation
Modern Continuous Threat Exposure Assessment and Validation platforms, such as NST Assure, are built to support this shift. These platforms are not collections of point tools. They are outside-in, adversary-aware systems designed to continuously assess, validate, and reduce real-world exposure.
They typically combine:
- →Agentic AI to predict attack paths and validate exploitability
- →Outside-in discovery that reflects real attacker visibility
- →Dynamic prioritization based on exploit activity, asset criticality, and business impact
- →Closed-loop execution connecting discovery, validation, and remediation
Together, these capabilities transform exposure data into validated, continuously updated trust signals —closing the gap between identifying risk and proving resilience. This is how platforms like NST Assure enable always-on digital trust scoring, where trust is no longer claimed periodically, but measured and demonstrated continuously.